It’s the kind of clever, off-the-cuff comment I’ve come to expect from my youngest son. He’s funny and wry and we were watching some pretty silly commercials on the cartoon […]
Category Archives: Blog
While we don’t want to have a stranglehold on your employees or the tools they use, we do want you to know what the pros and cons are and how using the cloud can expose you and your company to risk and added expense.
I’m still not too worried about killer robots quite yet, but as a Business Technologist, it puts me in an interesting position.
Look, I might wait and see how quantum computing works out before I recommend it to my clients, but upgraded operating systems, better networking tools, and new server platforms are not radically new technologies. You should always be ready to upgrade, get the newest version, and be as up-to-date as possible.
The crew of the U.S.S. Enterprise weren’t soldiers, or space pilots, or builders. They were knowledge workers. People who are paid to think and solve problems for a living. Just like people in the I.T. business.
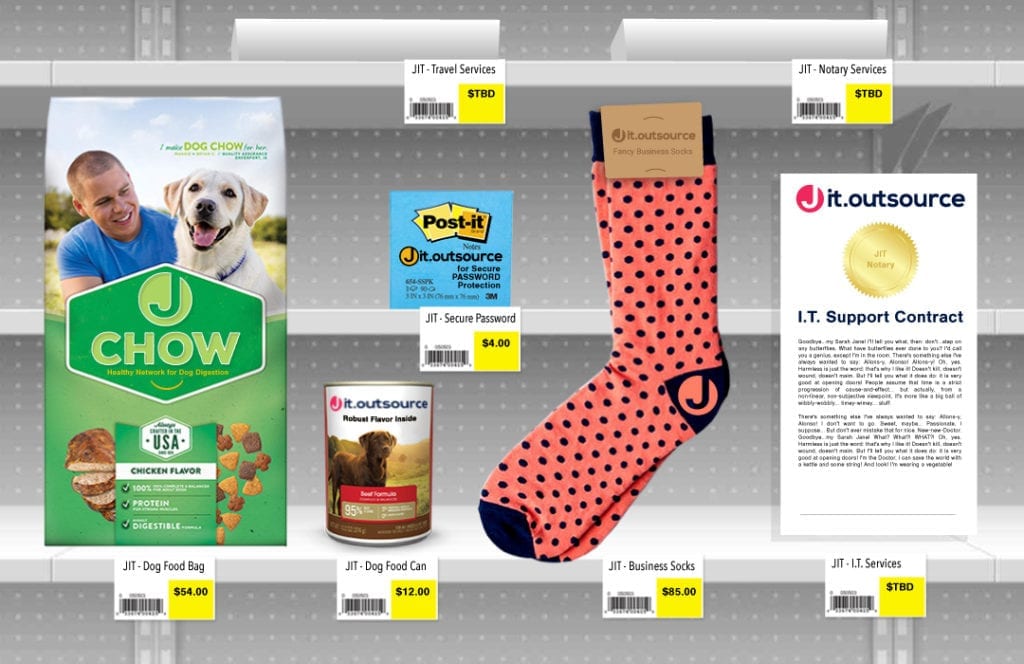
You don’t want us to sell footwear, pet care, or emergency repair. You want us to be very, very good at doing what we do which is supporting the core technologies that make a modern business competitive and proficient.
They call it “Five 9’s.” Guess what? No one cares about 99.999% uptime anymore. Unless they want to fly safely, make money, or read reliable news. FIVE MINUTES AND 15 […]
Gambling cost one of my (now former) clients $28,000. Plus two weeks – or more – of complete downtime for his business. It practically wasn’t “gambling.” In Vegas, even the […]
Smart homes are popping up everywhere. Nowadays everything can become automated thanks to digital assistants. And more gadgets are being released everyday with the intention of automating different household appliances, […]
Microsoft isn’t the only company actively protecting U.S. citizens from foreign hackers. Aside from the threat to the upcoming U.S. midterm elections, which Microsoft is handling with free cybersecurity applications, […]